A couple of years ago, all people wanted to hear about was social. Share links were being added to everything. Of course there’s no arguing with the significance of social. But it seemed clear that so much of our private communication was moving to the Net with scant protection from prying eyes — co-workers, friends, kids, the government, et al. And most of one’s communications went through just a few media — email, txt, Facebook, maybe a few others — which meant that leaving one of those platforms open on screen revealed too much. Moreover, I found it annoying to maintain a conversation by email. Messages would come in whenever, between spam and business notes and amazon receipts. If a thoughtful message from my friend Steven came in, I’d flag it to read and respond to later, when I wasn’t in the middle of five other things.
I called the solution Tunnel X to represent a private connection between two people. But it was only a concept and design until I met Steve Schneider, almost a year ago. Steve is a veteran CTO who got the idea immediately (my experience has been that some people get it immediately while some, particularly some technical types like my Google-employed hackathon partner a year ago, scoff at the idea of fixating on privacy— they are social zealots). We quickly allied and began to build tunnelx.com. Just before the new year, we launched the public beta, and I invite you to give it a try!
How is Tunnel X different from other ways of having an online conversation?
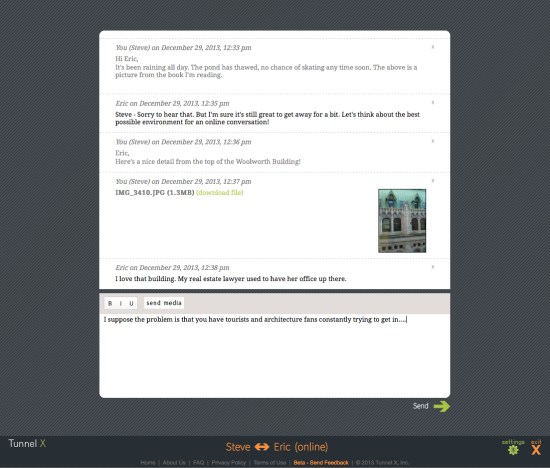
First, a tunnel (an account) consists of exactly two conversing confidants. There is no notion of an address or handle (like eric@tunnelx.com or @liftin). This would give you an identity on the system that could be tracked and that mixes messages together. If you want to converse with multiple people, you create multiple, unrelated tunnels. This segregation protects you. We also protect you with our sign-in ritual. Instead of picking a username and password (people tend to pick easily guessed passwords), you use an image that you have created (a digital photo) plus a PIN for good measure.
We ask nothing about you. Not your name, not your email address. All your messages are encrypted , and only you and your confidant can access the key to decrypt them. We cannot. You may be surprised to learn that most messaging platforms do not encrypt stored messages. In fact some services, like gmail, use your message content to target advertising. I think of a tunnel as a room with two keys, shared by the two confidants.
Your messages are preserved in a dialogue in your tunnel. I am not a fan of the disappearing message, à la Snapchat, because a) this kind of security is false — anyone can record the message if they are determined and b) I am interested in more serious messages that you may want to read twice and refer back to. Snapchat is more appropriate for teen gossip, where the inconvenience of capturing curbs the endless ricocheting of rumors. I hope that people find the simple experience of corresponding on Tunnel X to be the most satisfying, even pleasurable, way to carry on an online conversation. By the way, this conversation may be “asynchronous,” where we leave messages for each other to be read at our leisure, or “synchronous,” where we are online simultaneously, as in a chat room.
Eerily, the news cycle has obliged us with a daily barrage of Net security headlines over the last several months, from Ed Snowden to the Chris Christie traffic scandal. These days it is much easier to explain why we are doing this. Privacy is not only for outlaws. It is a right that has been eroded by the ubiquity of personal data.
Try Tunnel X, and tell us what you think!